Empowering ITQuickly VisualizeEasily Manage PrivilegeEffortless PatchingEffective Change
at Every Endpoint

Products
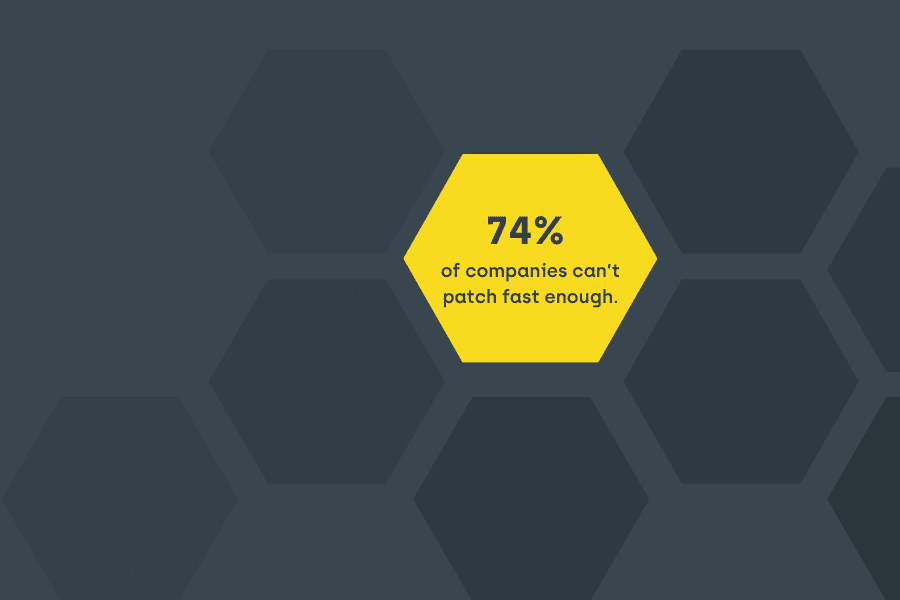
Defend Against Vulnerabilities at Scale
The secret to any great defense is a great offense. Recast Software’s comprehensive suite of solutions gives IT teams the edge they need to take their security posture beyond alerting and monitoring.
Features
Empowering IT at Every Endpoint
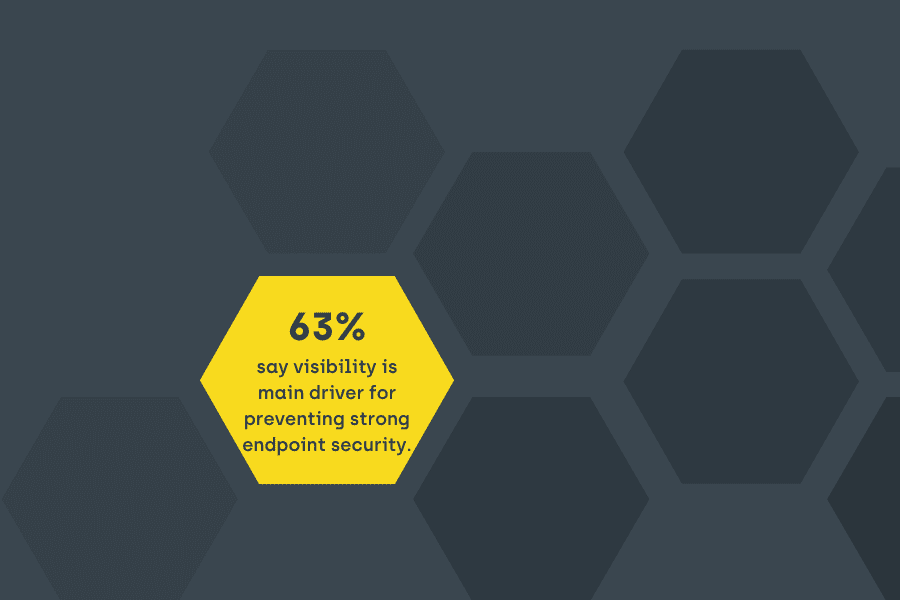
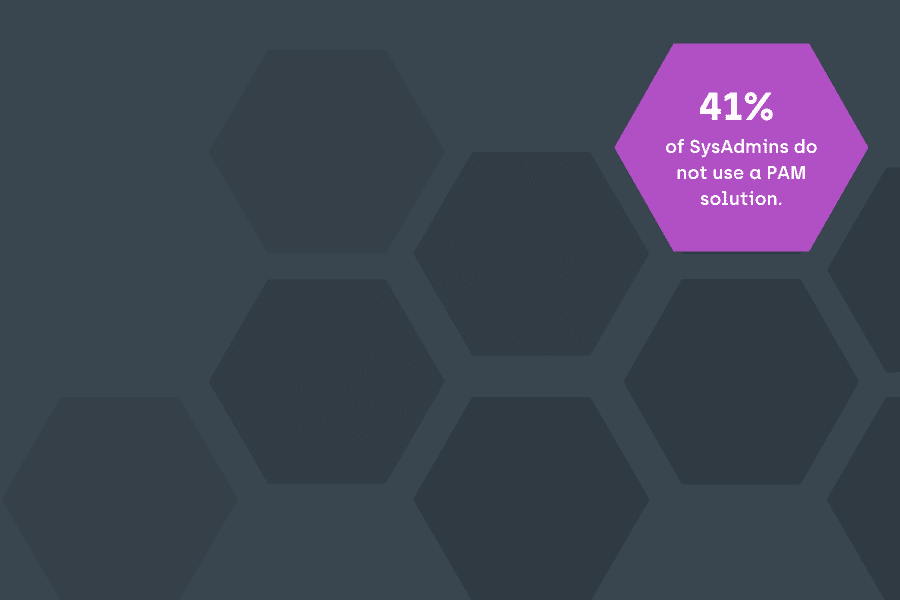
Endpoint security starts with clear insight – it’s understanding the environment and its unique variables. We have worked alongside IT professionals for years and are helping to increase enterprises’ control of the devices and users with four main solutions.


Quickly Visualize
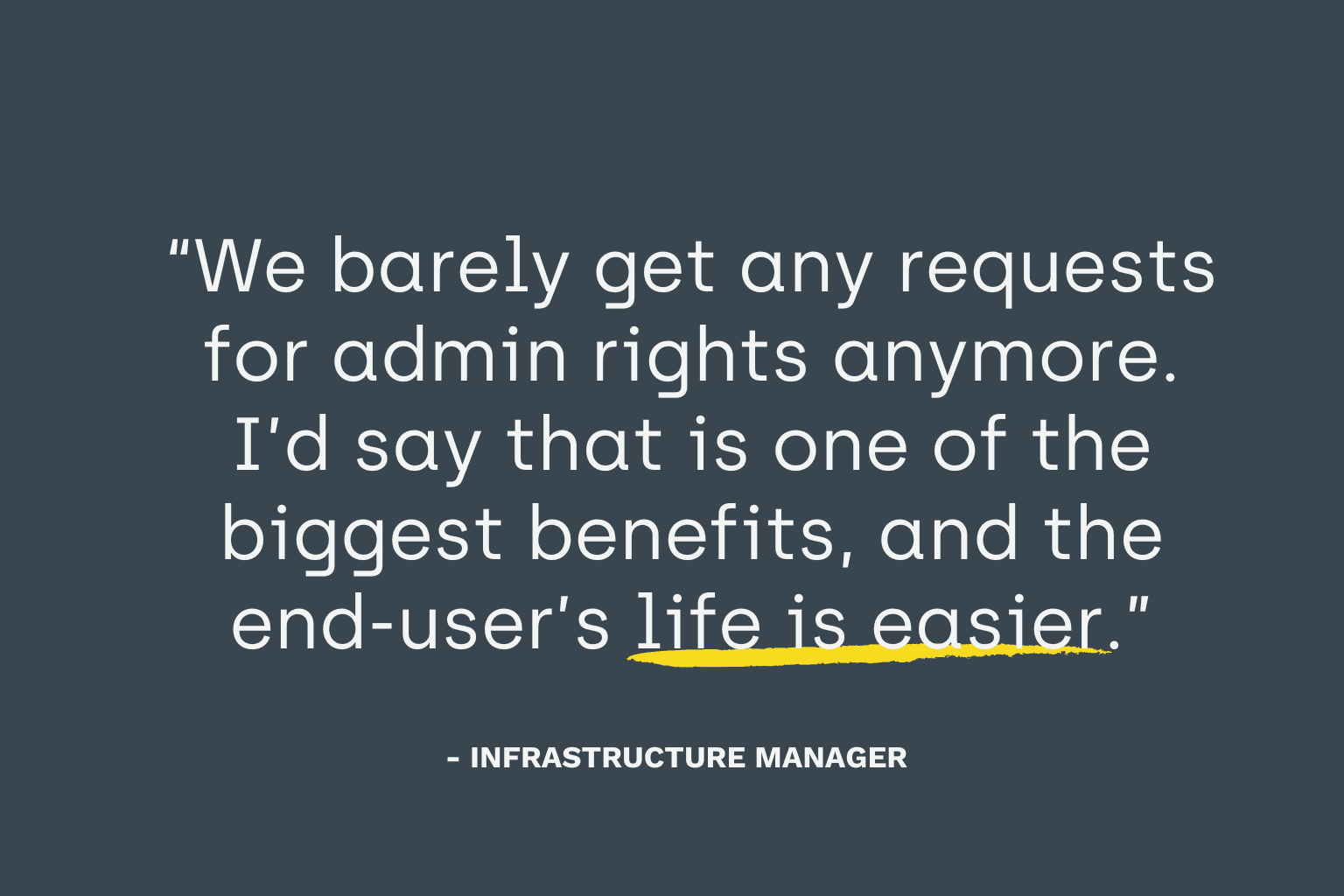
Easily Manage Privilege
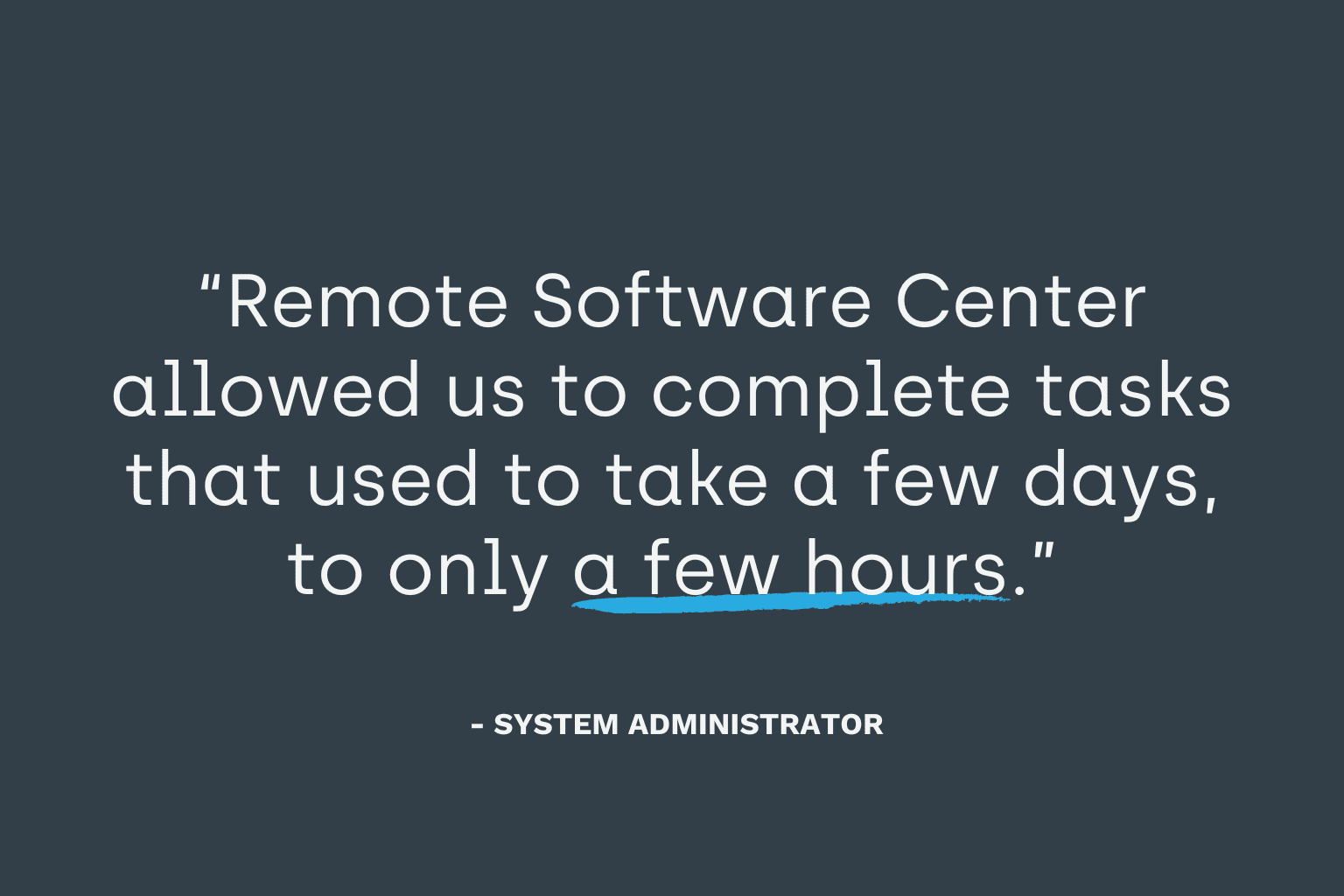
Effortless Patching
Effective Change
Solutions
You know us for our Right Click Tools. Now discover all we have to offer.
With products that currently impact over 60 million devices and the IT teams that manage them, we enable IT professionals to reduce downtime, gain powerful insights, and manage devices like never before.
We know endpoint management software.
When IT’s life is easier, everyone’s life is easier. Whether our suite of products are used to solve a calamity or an everyday task, we know that IT professionals require products that proactively improve the way endpoints are managed. That’s why we’re trusted by some of the world’s biggest organizations to get more out of Microsoft Configuration Manager.

Turn your IT team into an organizational powerhouse.
We understand the gravity of security and compliance within your organization. Our endpoint management software solutions supercharge your IT team with increased visibility, faster remediation times, and more efficient workflows. Every enterprise is different and faces unique challenges. But our full suite of endpoint management tools gives you the flexibility to readily meet those demands.

By the numbers
10M+
125+
70K+
60M
90%+
Let’s talk pricing.
You’ve done the research. Now let’s take the next step to help you uncover critical intel, reveal vulnerabilities, and quickly remediate issues. Request a quote today to get customized pricing for your organization.




























































